Bluetooth SMP security management
Smp is the Security Manage Protocol. Bluetooth is used for security management, which defines the process implementation of pairing and key distribution. Smp is used in LE-only devices or Bluetooth dual-mode devices.
frameFirst look at the framework of SM in ble (it seems to use ble to use SM):

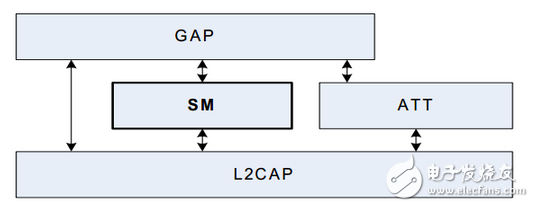
The front is a brief look at the general framework of ble SM, this part will explain in more detail how the implementation of ble's security management is. Next, security management may be referred to by SM.
Key distribution method to achieveSM, is to use a key distribution method to achieve the function of identifying ble data encryption and decryption. After the connection is established, the two parties negotiate a common key in some way, and then use the key to encrypt the data to be transmitted later by the encryption algorithm. The data actually transmitted to the air is the encrypted data, and the data is received. After that, you must decrypt it with the correct key to get the correct data. Of course, this way of encryption, the way to crack is to get its key.
Pairing – PairingThe pairing process is used to establish a key, that is, to complete the key agreement between the two parties, and to achieve a common process for the key. Pairing is actually divided into three sub-processes. Let's first look at the overall situation of the pairing process (initiator is the connection initiator, usually Master, Responder is Slave):
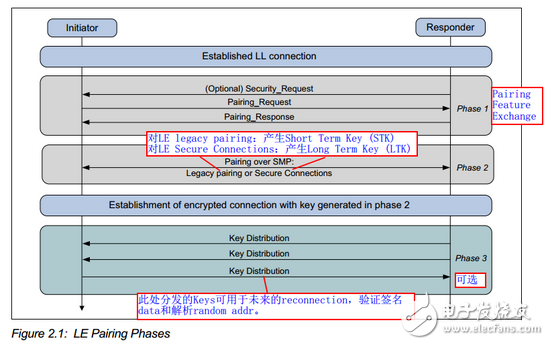
Here we need to explain the difference between the two in the above picture:
LE Secure ConnecTIon is a new feature after BT 4.2. The Key generation method is different. In addition, BR/EDR and LE can borrow the paired keys from each other. In short, there is a big improvement in security.
Pairing the first stage: pairing feature exchange
That is, you need to know which pairing functions are supported by the other party, such as authenTIcation requirements, IO capabilities, whether to support Secure Connection, etc., so that the two parties can perform corresponding pairing operations. For example, you can't have a device without input function use PIN code input for pairing...
Pairing the second stage: Key generation
LE Legacy pairing: generating Short Term Key;
LE Secure Connection: Generates a Long Term Key.
Pairing the third stage: Key distribution
Distribute Keys for other purposes, like the Identity Resolving Key (IRK), which may be used for Random Address resolution (unsure, subsequent confirmation). However, when distributing these keys, the link must be encrypted at this stage. If it is not encrypted, the key is directly intercepted by the middle, and the subsequent can still be cracked. Therefore, it must be encrypted. The encrypted Key is the STK or LTK generated in the second stage, or the Key generated by the BR/EDR pairing is directly shared under dual mode.
Example display
Here is the package that grabs the connection between the two devices (Master and Slave). The package part at the beginning of smp is the flow of the whole smp. For a detailed view:
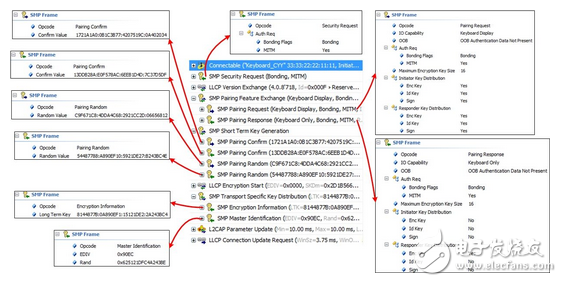
At the beginning, Advertiser sends ADV, then Scanner searches for ADV information, then transforms the Initiator to send Connect Request, and the connection is established. Subsequently, immediately, Slave sends a Security Request (optional), and then performs the first phase of pairing, exchanging the pairing support features. Then the second stage generates the STK (it seems that the device is used in the Legacy Pairing mode, after all, the current Secure Connection support 4.2 is not too much), the completion of the process can actually see the "LLCP Encryption Start" process, The link is encrypted immediately, and the encryption is completed before the third phase of pairing is performed, and other keys are distributed.
Password toolbox
These are tools (software or hardware unit implementations) for some encryption, random number generation, and some reusable small processes used in the pairing process. The password toolbox is full of password functions.
Here is a brief introduction to the cryptographic functions in this toolbox. If you want to implement the hardware circuit design of these functions, or coding, you should check the data in detail.
- ah: Generate a 24-bit hash value (random address generation and parsing will be used);
The following is for the LE Legacy pairing process:
- c1: a confirm value is generated during the pairing process;
- s1: STK is generated during the pairing process;
The following are for the LE Secure Connections pairing process:
- f4: The confirm value is generated during the pairing process;
- f5: LTK and MacKey are generated during the pairing process;
- f6: a check value is generated in the authentication process 2 during the pairing process;
- g2: a comparison value of 6 digits is generated in the authentication process 1 during the pairing process;
- h6: LTK for generating LE from BR/EDR link key, or BR/EDR link key for LEK from LE, which is equivalent to a Key conversion function.
The above cryptographic functions fall into two categories:
Security function e
Ah, c1, and s1 all belong to e. The way to encrypt data is as follows:
encryptedData = e(key, plaintextData) /* encrypteData, key, plaintextData are 128 bit data */
Security function AES-CMAC
F4, f5, f6, g2, h6 all belong to e, which is used as follows:
MAC = AES-CMACk(m)
The MAC is the Message Authentication Code (128 bit), m is the variable length data that needs to be authenticated, and k is the 128-bit Key.
Kitchen Hob,Gas Hobs,Gas Cooker Hob,Four Burner Gas Stove
xunda science&technology group co.ltd , https://www.gasstove.be